I’ve always been the type to casually plug in flash drives lying around to check what’s on them without having any second thoughts. That changed the day I watched a USB stick destroy a handful of devices like it was nothing. I didn’t witness this in person, but what I saw was real enough to shake me. Ever since then, I haven’t treated USB drives the same way.
Here’s what happened and why I now think twice (and usually a third time) before plugging anything in.
The Day I Learned That a USB Drive Could Kill Your Computer
Thanks to the nature of my work, you’ll often catch me watching random tech videos on YouTube. One day, I stumbled on a video by Austin Evans that made me physically recoil. He was showcasing a device called the USB Killer, and it looked like any other USB flash drive—nothing suspicious on the surface.
But where it gets interesting is that inside that innocent shell are capacitors designed to draw power from your device and then violently discharge it right back into the port. That burst of power is often enough to fry the internal hardware instantly.
The video showed laptops, smartphones, a Nintendo Switch Lite, and even a PS5 getting utterly destroyed, sometimes with audible clicks or cracks as components gave out. The newer USB Kill V4 model was even more powerful. It could be manually triggered and was capable of destroying devices even if they were turned off, as long as they had internal batteries or standby power.
Needless to say, I was rattled.

Related
Don’t Panic, But All USB Devices Have a Massive Security Problem
USB devices are apparently more dangerous than we’ve ever imagined.
USB Kill Devices Are Legal and Shockingly Easy to Buy
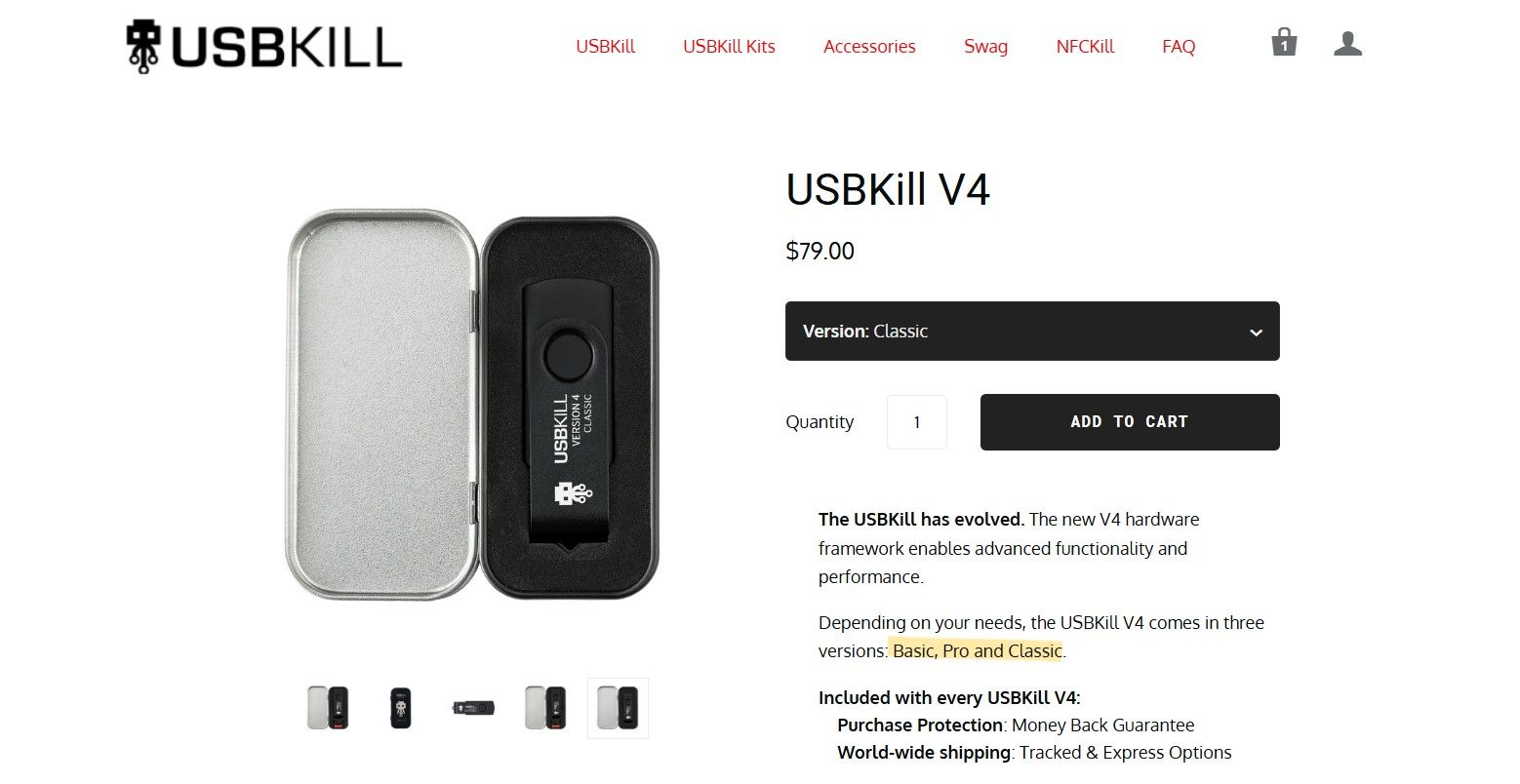
Out of curiosity (and a bit of paranoia), I checked the manufacturer’s website, USBKill. That’s when it got even more disturbing: these things are totally legal to buy and shockingly easy to order online. You don’t require any special license, work in cybersecurity, or prove any technical qualifications. You can just click “Buy Now,” and it ships to your doorstep. There are absolutely no restrictions.
Their cheapest kit, as of the time of writing, costs about $79. They’re marketed as “testing tools” for device hardening and surge protection. Interestingly, the company claims that over 95% of devices fail their USB surge tests.
Although there are warnings that the killer stick “should be treated with appropriate precautions,” that’s hardly a deterrent. There’s nothing stopping someone from using one for sabotage. In fact, there have been real-world cases of abuse. In 2019, a student in Albany used a USB Kill stick to destroy 66 computers, monitors, and podiums at his former college. He pleaded guilty, served a year in prison, and was ordered to pay over $58,000 in damages.
That story stuck with me. The accessibility of something so destructive made me rethink just how much blind trust I placed in USB drives.

Related
BadUSB: The Cyber Threat That Gets You To Plug It In
A recent spate of USB-based cyberattacks has hit organizations in the US.
No Antivirus Can Save You
Another thought that hit me hard was: “No antivirus (no matter how expensive, aggressive, or cutting-edge) on Earth could’ve stopped that.” We’re so used to thinking in terms of software threats like viruses, malware, and ransomware that, naturally, our defenses focus on code. But a USB Kill stick isn’t playing that game. It doesn’t sneak around your firewall or hide in some shady download. It attacks the hardware directly, sending a surge of electricity through the USB port to physically fry internal components. They don’t even need your computer to be turned on in some cases, especially with those with internal batteries, like the USBKill V4.
As seen in the video, some devices, like Apple products and the Samsung Z Flip 3, showed better hardware resilience. But this was due to physical design, not software.
Related
Is Third-Party Windows Antivirus Still Worth It in 2025?
Has Windows Defender rendered competing antivirus obsolete?
Not All USB Threats Are Kill Sticks
After watching one too many videos of devices being zapped into oblivion, I started researching other USB-based threats, and wow, the rabbit hole goes deep. There’s a whole buffet of malicious USB devices out there, and not all of them go for the dramatic “fry-your-motherboard” approach. Some are sneakier.
Take a USB Rubber Ducky, for example. It looks just like regular flash drives, but it’s actually a programmable keystroke injection tool. The moment you plug one in, it starts firing off commands like an invisible hacker at your keyboard, opening terminals, downloading malware, and creating new users. And it all happens in seconds. It doesn’t rely on software vulnerabilities. It just pretends to be a keyboard, which most computers trust by default.
Then there are devices like Bash Bunnies and O.MG cables. These are USB tools that blur the line between penetration testing gear and hacker toys. These can create fake network adapters, exfiltrate data, or set up backdoors without you ever noticing.
So yes, the USB Kill stick might be the most dramatic, but it’s far from the only threat hiding in plain sight.
You Can Protect Yourself With This Personal USB Safety Checklist
After learning all this, I had to rethink my everyday habits. I didn’t want to live in fear, but I definitely didn’t want to be careless either. So I came up with a simple, low-paranoia USB safety checklist that I now follow religiously:
- Don’t plug in random USB drives: This one’s obvious, but it’s also the easiest to ignore. If I find a flash drive on the ground or in some drawer and I don’t know where it came from, it’s not going anywhere near my laptop.
- Label your USB drives: I use masking tape and a marker to label mine. That way, I don’t confuse a random drive for one of my own. It sounds small, but it prevents a lot of second-guessing.
- Only use trusted chargers and cables: Even charging cables can be weaponized (you should really look up O.MG cables—they’re terrifying). I stick to ones I’ve bought myself or received from reputable brands.
- Disable autorun for USB devices: This helps stop rogue devices from automatically executing code when plugged in.
- Use USB data blockers when charging in public: These little adapters (sometimes called “USB condoms”) let power through but block data connections, which is perfect for public charging stations.
- Keep backups: Because even with precautions, accidents (and very determined attackers) happen.
Trusting a USB port now feels like trusting a stranger with your house keys. I’d rather be paranoid than powerless.

Related
Why Your Phone Charging Cable Needs a USB Condom
No, it’s not a joke. Yes, we’re serious. You gotta wrap your charging cable up.
What to Do If You Think You Plugged In Something Bad
If you ever get that sinking feeling, like “Wait… I shouldn’t have plugged that in,” don’t panic, but do act fast. First, unplug the device immediately if your system starts acting strangely or if anything starts executing on its own, and power down the computer to limit further damage or data leaks. If you’re on a work machine, report it to IT immediately. If it’s your personal device, consider running a thorough malware scan, changing your passwords (especially if you had any stored or autofilled), and monitoring for suspicious activity.
In the worst-case scenario, especially if you suspect something like a USB Killer, be prepared to get your hardware checked out or even replaced. The faster you act, the less damage you’re likely to face.
I’ve learned that not everything that fits in a port deserves your trust. I don’t plug things in lightly, and after reading this, maybe you won’t either.







Leave a Comment
Your email address will not be published. Required fields are marked *