Your ISP knows when you use Tor—it just can’t see what you’re doing when you’re using it. So while using Tor Browser and the Tor Network makes you feel completely anonymous, you might be surprised by its limitations and how using it can catch you out.
How Tor Hides Your Activity from Your ISP
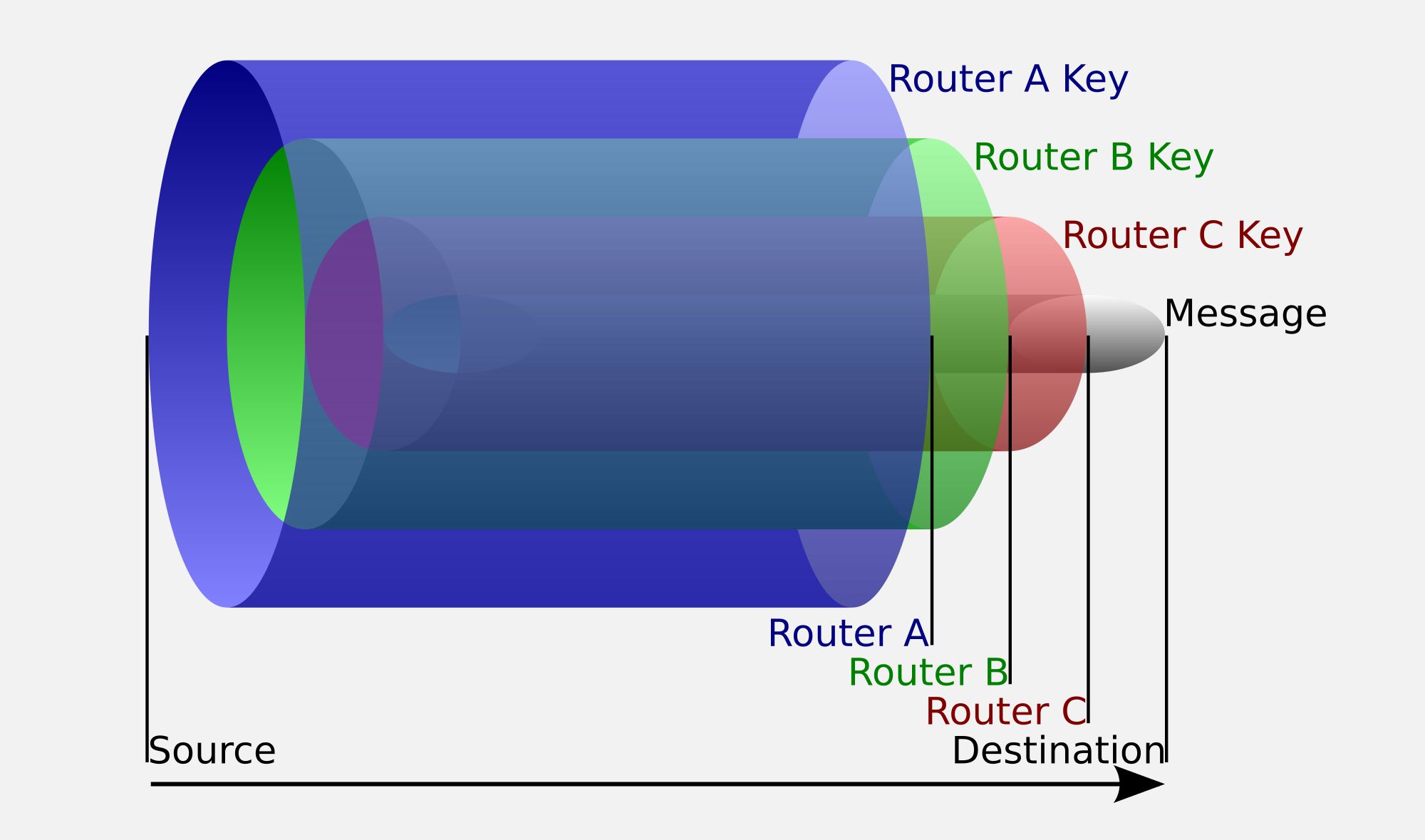
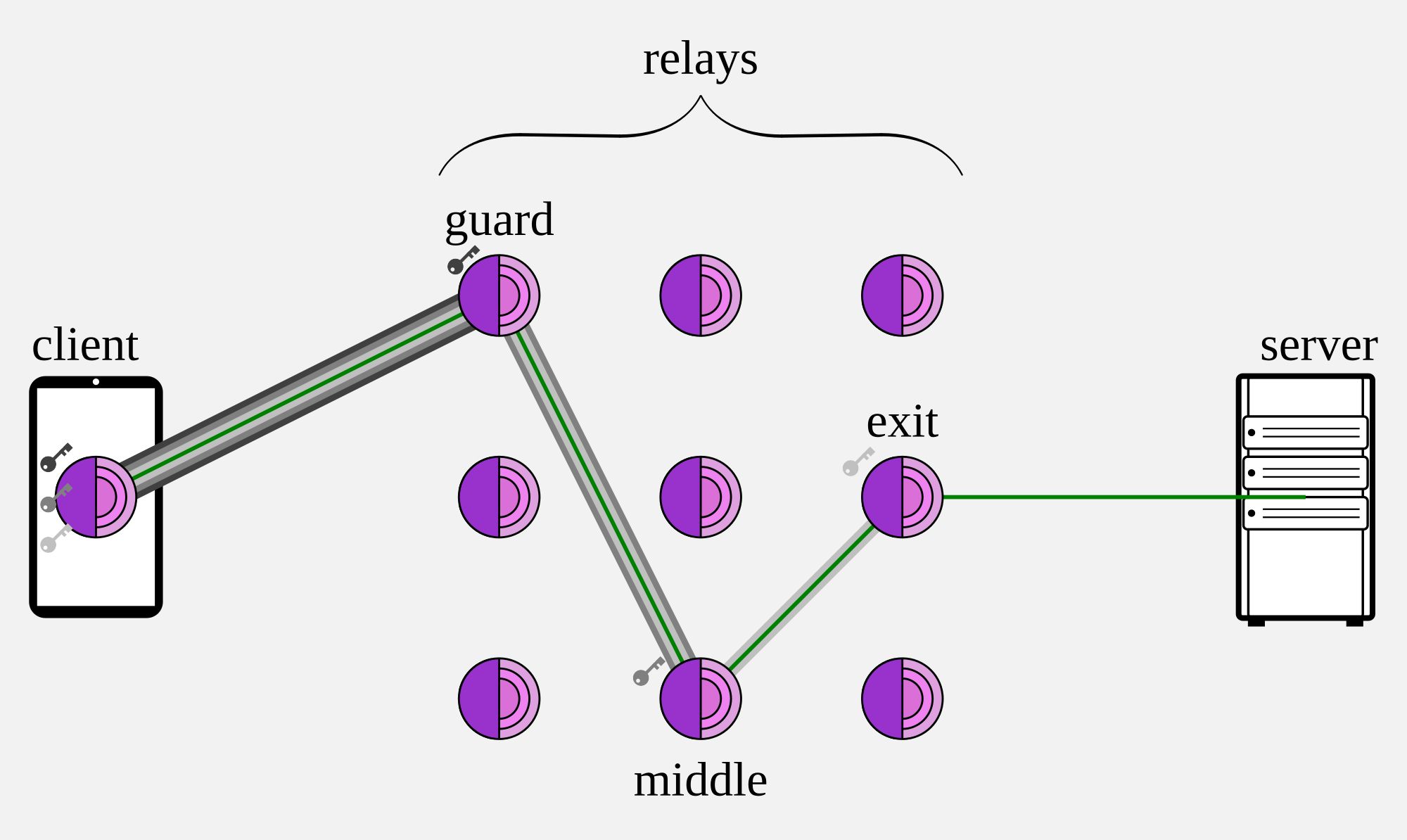
Tor operates by routing your internet traffic through multiple servers before it reaches its final destination. When you use Tor, your data gets encrypted in three layers and passes through three different types of nodes: the entry node, middle node, and exit node. Each node only knows where the data came from and where it needs to go next, but no single node knows the complete path from your computer to the website you’re visiting.
Here’s how this process actually works. When you want to visit a website using Tor, your browser first encrypts your request three times using the public keys from each of the three nodes it plans to use. Your computer sends this triple-encrypted package to the entry node, which removes the first layer of encryption and forwards the data to the middle node. The middle node strips off the second layer and sends it to the exit node, which removes the final layer and forwards your request to the actual website.
This system prevents your ISP from seeing which websites you’re visiting, as it only sees encrypted traffic going to the first Tor node. Your ISP knows you’re connecting to a Tor entry node, but it can’t see that you’re actually trying to reach Facebook, Gmail, or any other specific website. The website you visit sees the IP address of the exit node, not your real IP address, which helps protect your identity from the websites themselves.
The encryption Tor uses makes it nearly impossible for your ISP to decrypt your traffic and figure out what you’re doing online. Even if your ISP wanted to intercept and analyze your data, it would only see scrambled information that doesn’t reveal your actual browsing activity.
What Your ISP Can (and Can’t) See When You Use Tor
While Tor does an excellent job of hiding your browsing activity, your ISP can still detect certain things about your internet usage. It can tell that you’re using Tor in the first place because your ISP can see that you’re connecting to known Tor entry nodes. Most Tor entry nodes are publicly listed, so ISPs can easily check if you’re connecting to one of these servers.
Your ISP can also see how much data you’re sending and receiving while using Tor, along with the time of your connections. It knows when you start using Tor, how long you stay connected, and roughly how much traffic passes through during your session. This metadata doesn’t reveal which specific websites you’re visiting, but it does provide a general picture of your Tor usage patterns.
However, there are important limitations to what your ISP can observe. It cannot see the specific websites you visit, the content you download, or the searches you perform while using Tor. Your ISP also can’t read your messages, see your login credentials, or access any other sensitive information you transmit through the Tor network because your data is encrypted before leaving your computer.
If you want to prevent your ISP from knowing that you’re using Tor, consider using a VPN. A VPN acts as a secure tunnel between your device and the internet, which is one of the main reasons to subscribe to a reputable VPN service. When you connect to Tor through a VPN, your ISP will only see that you’re connected to a VPN server, not that you’re using Tor. This makes your activity appear like ordinary VPN traffic, reducing the likelihood of drawing attention or suspicion from your ISP.
Is Tor Safe to Use?
Tor is safe to use and offers strong privacy protection, but it’s not flawless. The easiest and most reliable way to use Tor is through the official Tor Browser, which is designed to keep your connection secure and your identity private. If you try other ways to access the Tor network, you need to be careful with your settings and understand how your tools work, since mistakes or poor cyber hygiene can weaken your privacy.
When it comes to possible conflict with the law, Tor itself is completely legal to use in the United States and most other countries. Law enforcement agencies and authoritarian governments sometimes try to block or monitor Tor usage, but using the software won’t get you in legal trouble in most places. Though any country with strong laws surrounding encryption will certainly differ, such as China, Russia, Iran, Belarus, and Turkmenistan. Always check local laws before firing up Tor, as you may be breaking the law without realizing.
Many legitimate users rely on Tor, including journalists, activists, and privacy-conscious individuals who want to protect their online activities from surveillance. So, you shouldn’t be worried when using Tor.

Related
These Are My 9 Tips on Using the Tor Network Safely
The dark web sounds fun, but there are some important security steps you need to take first.
However, the software does have some practical drawbacks that you should consider. Tor connections are significantly slower than regular internet browsing because your traffic has to bounce through multiple servers. Some websites also block connections from known Tor exit nodes, which means you might not be able to access certain services while using the browser.
Overall, Tor offers solid protection for users who need anonymity online, but you should understand its limitations and use it as part of a broader privacy strategy rather than relying on it as your only security tool.




:max_bytes(150000):strip_icc()/productivity-21d337f44d884a2bb9a3e5a6d3ccce7e.png?w=1174&resize=1174,862&ssl=1)


Leave a Comment
Your email address will not be published. Required fields are marked *